ITIL
ITIL, formerly an acronym for Information Technology Infrastructure Library, is a set of practices for IT service management (ITSM) that focuses on aligning IT services with the needs of business. In its current form (known as ITIL V3), ITIL is published as a series of five core volumes, each of which covers a different ITSM lifecycle stage. Although ITIL underpins ISO/IEC 20000 (previously BS 15000), the International Service Management Standard for IT service management, there are some differences between the ISO 20000 standard and the ITIL framework.
ITIL describes processes, procedures, tasks, and checklists which are not organization-specific, but can be applied by an organization for establishing integration with the organization's strategy, delivering value, and maintaining a minimum level of competency. It allows the organization to establish a baseline from which it can plan, implement, and measure. It is used to demonstrate compliance and to measure improvement.
Since July 2013, ITIL has been owned by AXELOS, a joint venture between Capita and the Cabinet Office. AXELOS licenses organisations to use the ITIL intellectual property, accredits licensed examination institutes, and manages updates to the framework. Organizations that wish to implement ITIL internally do not require this license.
History
Responding to growing dependence on IT, the UK Government's Central Computer and Telecommunications Agency (CCTA) in the 1980s developed a set of recommendations. It recognized that, without standard practices, government agencies and private sector contracts had started independently creating their own IT management practices.
The IT Infrastructure Library originated as a collection of books, each covering a specific practice within IT service management. ITIL was built around a process model-based view of controlling and managing operations often credited to W. Edwards Deming and his plan-do-check-act (PDCA) cycle.[1]
After the initial publication in 1989–96, the number of books quickly grew within ITIL v1 to more than 30 volumes.
In 2000/2001, to make ITIL more accessible (and affordable), ITIL v2 consolidated the publications into nine logical "sets" that grouped related process-guidelines to match different aspects of IT management, applications and services. The Service Management sets (Service Support and Service Delivery) were by far the most widely used, circulated, and understood of the ITIL v2 publications.
- In April 2001, the CCTA was merged into the OGC, an office of the UK Treasury.[2]
- In 2006, the ITIL v2 glossary was published.
- In May 2007, this organization issued version 3 of ITIL (also known as the ITIL Refresh Project) consisting of 26 processes and functions, now grouped into only 5 volumes, arranged around the concept of Service lifecycle structure. Version 3 is now known as ITIL 2007 Edition.
- In 2009, the OGC officially announced that ITIL v2 certification would be withdrawn and launched a major consultation as per how to proceed.[3]
- In July 2011, the 2011 edition of ITIL was published, providing an update to the version published in 2007. The OGC is no longer listed as the owner of ITIL, following the consolidation of OGC into the Cabinet Office.
Overview of ITIL 2007 edition
ITIL 2007 edition (previously known as version 3) is an extension of ITIL v2 and fully replaced it following the completion of the withdrawal period on 30 June 2011.[4] ITIL 2007 provides a more holistic perspective on the full life cycle of services, covering the entire IT organization and all supporting components needed to deliver services to the customer, whereas v2 focused on specific activities directly related to service delivery and support. Most of the v2 activities remained untouched in 2007, but some significant changes in terminology were introduced in order to facilitate the expansion.
Changes and characteristics of the 2011 edition of ITIL
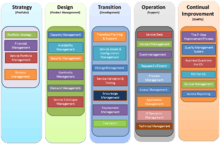
A summary of changes has been published by the UK Government. In line with the 2007 edition, the 2011 edition consists of five core publications – Service Strategy, Service Design, Service Transition, Service Operation, and Continual Service Improvement. ITIL 2011 is an update to the ITIL framework that addresses significant additional guidance with the definition of formal processes which were previously implied but not identified, as well as correction of errors and inconsistencies.
Twenty-six processes are listed in ITIL 2011 edition and described below, along with which core publication provides the main content for each process.
ITIL 2007 has five volumes, published in May 2007, and updated in July 2011 as ITIL 2011 for consistency:
- ITIL Service Strategy: understands organizational objectives and customer needs.[5]
- ITIL Service Design: turns the service strategy into a plan for delivering the business objectives.[6]
- ITIL Service Transition: develops and improves capabilities for introducing new services into supported environments.[7]
- ITIL Service Operation: manages services in supported environments.[8]
- ITIL Continual Service Improvement: achieves services incremental and large-scale improvements.[9]
Due to the similarity between ITIL v3 of 2007 and ITIL 2011, no bridge examinations for ITIL v3 certification holders were created or made available for ITIL 2011 certification.
Service strategy
The center and origin point of the ITIL Service Lifecycle, the ITIL Service Strategy (SS) volume,[5] provides guidance on clarification and prioritization of service-provider investments in services. More generally, Service Strategy focuses on helping IT organizations improve and develop over the long term. In both cases, Service Strategy relies largely upon a market-driven approach. The Service Strategy lifecycle stage is often considered as the core of the service lifecycle. In Service Strategy stage, the strategic approach for the whole lifecycle is identified to provide values to the customers through IT service management. Key topics covered include service value definition, business-case development, service assets, market analysis, and service provider types. List of covered processes:
- Strategy management for IT Services
- Service portfolio management
- Financial management for IT services
- Demand management
- Business relationship management
For candidates in the ITIL Intermediate Capability stream, the Service Offerings and Agreements (SOA) Qualification course and exam are most closely aligned to the Service Strategy (SS) Qualification course and exam in the Lifecycle stream.
Service Portfolio Management
The customer needs services to achieve its objectives. The service provider should ensure it can provide these services. The purpose of Service Portfolio Management is ensuring these services are offered.
The service portfolio contains the services managed by the service provider. The service portfolio comprises: the pipeline section, which contains the services that are yet to be offered; the service catalog section, which contains the details of operational services; and the retired section, which contains details of the services that are no longer offered.–
Financial management for IT services
IT Financial Management comprises the discipline of ensuring that the IT infrastructure is obtained at the most effective price (which does not necessarily mean cheapest) and calculating the cost of providing IT services so that an organization can understand the costs of its IT services. These costs may then be recovered from the customer of the service. This is the 2nd component of service delivery process.
Service design
The Service Design (SD) volume[6] provides good-practice guidance on the design of IT services, processes, and other aspects of the service management effort. Significantly, design within ITIL is understood to encompass all elements relevant to technology service delivery, rather than focusing solely on design of the technology itself. As such, service design addresses how a planned service solution interacts with the larger business and technical environments, service management systems required to support the service, processes which interact with the service, technology, and architecture required to support the service, and the supply chain required to support the planned service. Within ITIL, design work for an IT service is aggregated into a single Service Design Package (SDP). Service design packages, along with other information about services, are managed within the service catalogues.
List of covered processes:
- Design coordination
- Service catalogue management
- Service-level management
- Availability management
- Capacity management
- IT service continuity management
- Security management
- Supplier management
A model used to help define roles and responsibilities in service design is a RACI matrix (Responsible, Accountable, Consulted and Informed).
Service catalogue management
Service catalogue management maintains and produces the service catalogue and ensures that it contains accurate details, dependencies and interfaces of all services made available to customers. Service catalogue information includes:
- ordering and requesting processes
- prices
- deliverables
- contract points
Service-level management
Service-level management provides for continual identification, monitoring and review of the levels of IT services specified in the service-level agreements (SLAs). Service-level management ensures that arrangements are in place with internal IT support-providers and external suppliers in the form of operational level agreements (OLAs) and underpinning contracts (UCs), respectively. The process involves assessing the impact of change on service quality and SLAs. The service-level management process is in close relation with the operational processes to control their activities. The central role of service-level management makes it the natural place for metrics to be established and monitored against a benchmark.
Service-level management is the primary interface with the customer (as opposed to the user serviced by the service desk). Service-level management is responsible for:
- ensuring that the agreed IT services are delivered when and where they are supposed to be;
- liaising with availability management, capacity management, incident management and problem management to ensure that the required levels and quality of service are achieved within the resources agreed with financial management;
- ensuring that appropriate IT service continuity plans exist to support the business and its continuity requirements.
The service-level manager relies on the other areas of the service delivery process to provide the necessary support which ensures the agreed services are provided in a cost-effective, secure and efficient manner.
Availability management
Availability management allows organizations to sustain IT service-availability in order to support the business at a justifiable cost. High-level activities are realizing availability requirements, compiling availability plans, monitoring availability, and monitoring maintenance obligations.
Availability management addresses the ability of an IT component to perform at an agreed level over a period of time.
- Reliability: Ability of an IT component to perform at an agreed level at described conditions.
- Maintainability: The ability of an IT component to remain in, or be restored to an operational state.
- Serviceability: The ability for an external supplier to maintain the availability of component or function under a third-party contract.
- Resilience: A measure of freedom from operational failure and a method of keeping services reliable. One popular method of resilience is redundancy.
- Security: A service may have associated data. Security refers to the confidentiality, integrity, and availability of that data. Availability gives a clear overview of the end-to-end availability of the system.
Capacity management
Capacity management supports the optimum and cost-effective provision of IT services by helping organizations match their IT resources to business demands. The high-level activities include:
- application sizing
- workload management
- demand management
- modelling
- capacity planning
- resource management
- performance management
Capacity management is focused on strategic capacity, including capacity of personnel (e.g., human resources, staffing and training), system capacity, and component (or tactical) capacity.
IT service continuity management
IT service continuity management (ITSCM) covers the processes by which plans are put in place and managed to ensure that IT services can recover and continue even after a serious incident occurs. It is not just about reactive measures, but also about proactive measures – reducing the risk of a disaster in the first instance.
ITSCM is regarded by the application owners as the recovery of the IT infrastructure used to deliver IT services, but as of 2009 many businesses practice the much further-reaching process of business continuity planning (BCP), to ensure that the whole end-to-end business process can continue should a serious incident occur (at primary support level).
ITSCM involves the following basic steps:
- prioritising the activities to be recovered by conducting a business impact analysis (BIA)
- performing a risk assessment (aka risk analysis) for each of the IT services to identify the assets, threats, vulnerabilities and countermeasures for each service.
- evaluating the options for recovery
- producing the contingency plan
- testing, reviewing, and revising the plan on a regular basis.
Security management
The ITIL-process Security Management[10] describes the structured fitting of information security in the management organization. It is based on the code of practice for information security management system (ISMS) now known as ISO/IEC 27002.
A basic goal of security management is to ensure adequate information security. The primary goal of information security, in turn, is to protect information assets against risks, and thus to maintain their value to the organization. This is commonly expressed in terms of ensuring their confidentiality, integrity and availability, along with related properties or goals such as authenticity, accountability, non-repudiation and reliability.
Mounting pressure for many organizations to structure their information security management systems in accordance with ISO/IEC 27001 requires revision of the ITIL v2 security management volume, which culminated in the release of the 2007 edition.
Supplier management
The purpose of supplier management is to obtain value for money from suppliers and contracts. It ensures that underpinning contracts and agreements align with business needs, Service Level Agreements and Service Level Requirements. Supplier Management oversees process of identification of business needs, evaluation of suppliers, establishing contracts, their categorization, management and termination.
Service transition
Service transition (ST), as described by the ITIL service transition volume,[7] relates to the delivery of services required by a business into live/operational use, and often encompasses the "project" side of IT rather than business as usual (BAU). This area also covers topics such as managing changes to the BAU environment.
List of ITIL processes in service transition:
- Transition planning and support
- Change management
- Service asset and configuration management
- Release and deployment management
- Service validation and testing
- Change evaluation
- Knowledge management
Change management
Change management aims to ensure that standardised methods and procedures are used for efficient handling of all changes. A change is an event that results in a new status of one or more configuration items (CIs), and which is approved by management, is cost-effective, enhances business process changes (fixes) – all with a minimum risk to IT infrastructure.
The main aims of change management include:
- Minimal disruption of services
- Reduction in back-out activities
- Economic use of resources involved in the change
Common change management terminology includes:
- Change: the addition, modification or removal of CIs
- Request For Change (RFC) or, in older terminology, Change Request (CR): a form used to record details of a request for a change and is sent as an input to Change Management by the Change Requestor
- ITIL v2 - Forward Schedule of Changes (FSC): schedule that contains details of all forthcoming Changes.
- ITIL 2007 - Change Schedule (CS): schedule that contains details of all forthcoming Changes, and references historical data. Many people still refer to the known term FSC.
There are three types of changes: Standard Change,Normal Change,Urgent/Emergency Change
Service asset and configuration management
Service asset and configuration management is primarily focused on maintaining information (i.e., configurations) about Configuration Items (i.e., assets) required to deliver an IT service, including their relationships. Configuration management is the management and traceability of every aspect of a configuration from beginning to end and it includes the following key process areas under its umbrella:
- Identification
- Planning
- Change control
- Change management
- Release management
- Maintenance
Release and deployment management
Release and deployment management is used by the software migration team for platform-independent and automated distribution of software and hardware, including license controls across the entire IT infrastructure. Proper software and hardware control ensures the availability of licensed, tested, and version-certified software and hardware, which functions as intended when introduced into existing infrastructure. Quality control during the development and implementation of new hardware and software is also the responsibility of Release Management. This guarantees that all software meets the demands of the business processes. Release management utilizes Definitive Media Library for storage of software.
The goals of release management include:
- Planning the rollout of software
- Designing and implementing procedures for the distribution and installation of changes to IT systems
- Effectively communicating and managing expectations of the customer during the planning and rollout of new releases
- Controlling the distribution and installation of changes to IT systems
Release management focuses on the protection of the live environment and its services through the use of formal procedures and checks.
A Release consists of the new or changed software and/or hardware required to implement approved changes. Release categories include:
- Major software releases and major hardware upgrades, normally containing large amounts of new functionality, some of which may make intervening fixes to problems redundant. A major upgrade or release usually supersedes all preceding minor upgrades, releases and emergency fixes.
- Minor software releases and hardware upgrades, normally containing small enhancements and fixes, some of which may have already been issued as emergency fixes. A minor upgrade or release usually supersedes all preceding emergency fixes.
- Emergency software and hardware fixes, normally containing the corrections to a small number of known problems.
Releases can be divided based on the release unit into:
- Delta release: a release of only that part of the software which has been changed. For example, security patches.
- Full release: the entire software program is deployed—for example, a new version of an existing application.
- Packaged release: a combination of many changes—for example, an operating system image which also contains specific applications.
Service operation
Service Operation (SO) aims to provide best practice for achieving the delivery of agreed levels of services both to end-users and the customers (where "customers" refer to those individuals who pay for the service and negotiate the SLAs). Service operation, as described in the ITIL Service Operation volume,[8] is the part of the lifecycle where the services and value is actually directly delivered. Also the monitoring of problems and balance between service reliability and cost etc. are considered. The functions include technical management, application management, operations management and service desk as well as, responsibilities for staff engaging in Service Operation.
Processes
- Event Management
- Access Management
- Request Fulfillment
- Problem Management
- Incident Management
Functions
- Service Desk
- Technical Management
- Application Management
- IT Operations Management
Service desk
The service desk is one of four ITIL functions and is primarily associated with the Service Operation lifecycle stage. Tasks include handling incidents and requests, and providing an interface for other ITSM processes. Features include:
- single point of contact (SPOC) and not necessarily the first point of contact (FPOC)
- single point of entry
- single point of exit
- easier for customers
- streamlined communication channel
Primary purposes of a service desk include:
- incident control: life-cycle management of all service requests
- communication: keeping a customer informed of progress and advising on workarounds
The service desk function can have various names, such as:
- Call center: main emphasis on professionally handling large call volumes of telephone-based transactions
- Help desk: manage, co-ordinate and resolve incidents as quickly as possible at primary support level
- Service desk: not only handles incidents, problems and questions but also provides an interface for other activities such as change requests, maintenance contracts, software licenses, service-level management, configuration management, availability management, financial management and IT services continuity management
The three types of structure for consideration:
- Local service desk: to meet local business needs – practical only until multiple locations requiring support services are involved
- Central service desk: for organizations having multiple locations – reduces operational costs and improves usage of available resources
- Virtual service desk: for organizations having multi-country locations – can be situated and accessed from anywhere in the world due to advances in network performance and telecommunications, reducing operational costs and improving usage of available resources
Application management
ITIL application management[11] encompasses a set of best practices proposed to improve the overall quality of IT software development and support through the life-cycle of software development projects, with particular attention to gathering and defining requirements that meet business objectives.
Software asset management (SAM) is a primary topic of ITILv2 and is closely associated with the ITIL Application Management function. SAM is the practice of integrating people, processes, and technology to allow software licenses and usage to be systematically tracked, evaluated, and managed. The goal of SAM is to reduce IT expenditures, human resource overhead and risks inherent in owning and managing software assets.
SAM practices include:
- maintaining software license compliance
- tracking inventory and software asset use
- maintaining standard policies and procedures surrounding definition, deployment, configuration, use, and retirement of software assets and the definitive software library.
SAM represents the software component of IT asset management. This includes hardware asset management because effective hardware inventory controls are critical to efforts to control software. This means overseeing software and hardware that constitute an organization's computers and network.
IT Operations management
Refer to ICT infrastructure management for more details.
Technical management
Refer to ICT infrastructure management for more details.
Event management
An event may indicate that something is not functioning correctly, leading to an incident being logged. Events may also indicate normal activity, or a need for routine intervention such as changing a tape. Event management depends on monitoring, but it is different. Event management generates and detects notifications, while monitoring checks the status of components even when no events are occurring. Events may be detected by a CI sending a message, or by a management tool polling the CI. After an event has been detected it may lead to an Incident, Problem or Change, or it may simply be logged in case the information is needed. Response to an event may be automated or may require manual intervention. If actions are needed then a trigger, such as an SMS message or an incident being automatically logged, can alert support staff.
Incident management
Incident management aims to restore normal service operation as quickly as possible and minimise the adverse effect on business operations, thus ensuring that the best possible levels of service quality and availability are maintained. 'Normal service operation' is defined here as service operation within service-level agreement (SLA) limits.
An incident is defined as:
- 2007: An unplanned interruption to an IT service or a reduction in the quality of an IT service. Failure of a configuration item that has not yet impacted service is also an incident. For example, failure of one disk from a mirror set.
- V2: An event which is not part of the standard operation of a service and which causes or may cause disruption to or a reduction in the quality of services and customer productivity.
The objective of incident management is to restore normal operations as quickly as possible with the least possible impact on either the business or the user, at a cost-effective price. The transformation between event-to-incident is the critical junction where Application Performance Management (APM) and ITIL come together to provide tangible value back to the business.[12]
Request fulfillment
Request fulfillment (or request management) focuses on fulfilling Service Requests, which are often minor (standard) changes (e.g., requests to change a password) or requests for information.
The term "standard change" means pre-approved, repeatable, pre-defined, low risk changes. If the change does not meet these criteria then it is not a standard change and should be defined as a request for change.
Problem management
Problem management aims to resolve the root causes of incidents and thus to minimise the adverse impact of incidents caused by errors within the IT infrastructure, and to prevent recurrence of incidents related to these errors. A "problem" in this context is the unknown underlying cause of one or more incidents, and a 'known error' is a problem that is successfully diagnosed and for which either a work-around or a permanent resolution has been identified. The CCTA (Central Computer and Telecommunications Agency) defines problems and known errors as follows:
- A problem is a condition often identified as a result of multiple incidents that exhibit common symptoms. Problems can also be identified from a single significant incident, indicative of a single error, for which the cause is unknown, but for which the impact is significant.
- A known error is a condition identified by successful diagnosis of the root cause of a problem, and the subsequent development of a work-around.
Problem management differs from incident management. Problem management aims primarily to find and resolve the root cause of a problem and thus prevent further incidents; the purpose of incident management is to return the service to normal level as soon as possible, with smallest possible business impact.
The problem-management process reduces the number and severity of incidents and problems on the business, and documents the details of the problem and resolution to be available for the first-line and second-line of the help desk. The proactive process identifies and resolves problems before incidents occur. Such processes include:
- Trend analysis
- Targeting support action
- Providing information to the organization
The error control process iteratively diagnoses known errors until they are eliminated by the successful implementation of a change under the control of the Change Management process.
The problem control process aims to handle problems in an efficient way. Problem control identifies the root cause of incidents and reports it to the service desk. Other activities are:
- Problem identification and recording
- Problem classification
- Problem investigation and diagnosis
Root-cause analysis
Root-cause analysis is a formal problem-solving process and a critical component of Problem Management. Once a problem (or potential problem) has been identified, the root cause analysis process begins. The purpose of a root cause analysis is two-fold:
- develop a thorough understanding of the problem and its causes
- identify corrective/preventive actions that will reduce the risk of recurrence to an acceptable level
Classic root-cause analysis methods include the 5-whys and Ishikawa diagram or fishbone diagram. Others have since developed more advanced root cause analysis methodologies, some with corresponding software applications.
Benefits from employing a standard, structured root-cause analysis methodology include:
- common terms, language, and structure with respect to root cause analysis
- problem identification, including actual and potential impact
- identification of the problem's causes, their interactions, and the supporting evidence
- identification of corrective/preventive actions (CAPA) that will prevent recurrence of the problem
- development of a knowledge base which others can use as a resource
Identity management
Identity management (IdM) less commonly called Access and Identity Management (AIM) as a process focuses on granting authorised users the right to use a service, while preventing access to non-authorised users. Certain identity management processes execute policies defined in Security Management.
Continual service improvement (CSI)
Continual service improvement, defined in the ITIL continual service improvement volume,[9] aims to align and realign IT services to changing business needs by identifying and implementing improvements to the IT services that support the business processes. It incorporates many of the same concepts articulated in the Deming Cycle of Plan-Do-Check-Act. The perspective of CSI on improvement is the business perspective of service quality, even though CSI aims to improve process effectiveness, efficiency and cost effectiveness of the IT processes through the whole lifecycle. To manage improvement, CSI should clearly define what should be controlled and measured.
CSI needs upfront planning, training and awareness, ongoing scheduling, roles created, ownership assigned,and activities identified to be successful. CSI must be planned and scheduled as process with defined activities, inputs, outputs, roles and reporting. Continual Service Improvement and Application Performance Management (APM) are two sides of the same coin. They both focus on improvement with APM tying together service design, service transition, and service operation which in turn helps raise the bar of operational excellence for IT.[13]
Improvement initiatives typically follow a seven-step process:
- Identify the strategy for improvement
- Define what you will measure
- Gather the data
- Process the data
- Analyse the information and data
- Present and use the information
- Implement improvement
Overview of ITIL v2
The eight ITIL version 2 books and their disciplines are:
The IT service management sets
Other operational guidance
- 3. ICT infrastructure management
- 4. Security management
- 5. Application management
- 6. Software asset management
To assist with the implementation of ITIL practices a further book was published (Apr 9, 2002) providing guidance on implementation (mainly of Service Management):
And this has more recently (Jan 26, 2006) been supplemented with guidelines for smaller IT units, not included in the original eight publications:
- 8. ITIL small-scale implementation
Service support
The Service Support[14] ITIL discipline focuses on the User of the ICT services and is primarily concerned with ensuring that they have access to the appropriate services to support the business functions.
To a business, customers and users are the entry point to the process model. They get involved in service support by:
- Asking for changes
- Needing communication, updates
- Having difficulties, queries
- Real process delivery
The service desk functions are the single contact-point for end-users' incidents. Its first function is always to document ("create") an incident. If there is a direct solution, it attempts to resolve the incident at the first level. If the service desk cannot solve the incident then it is passed to a 2nd/3rd level group within the incident management system. Incidents can initiate a chain of processes: incident management, problem management, change management, release management and configuration management. This chain of processes is tracked using the configuration management database (CMDB), - ITIL refers to configuration management system (CMS), which records each process, and creates output documents for traceability (quality management). Note - CMDB/CMS does not have to be a single database. The solution can be Federated.
Service delivery
The service delivery[15] discipline concentrates on the proactive services the ICT must deliver to provide adequate support to business users. It focuses on the business as the customer of the ICT services (compare with: service support). The discipline consisted of the following processes:
- Service level management
- Capacity management
- IT service continuity management
- Availability management
- Financial management
ICT infrastructure management
Information and Communication Technology (ICT) management[16] processes recommend best practice for requirements analysis, planning, design, deployment and ongoing operations management and technical support of an ICT infrastructure.
The infrastructure management processes describe those processes within ITIL that directly relate to the ICT equipment and software that is involved in providing ICT services to customers.
- ICT design and planning
- ICT deployment
- ICT operations
- ICT technical support
These disciplines are less well understood than those of service management and therefore often some of their content is believed to be covered 'by implication' in service management disciplines.
ICT design and planning
ICT design and planning provides a framework and approach for the strategic and technical design and planning of ICT infrastructures. It includes the necessary combination of business (and overall IS) strategy, with technical design and architecture. ICT design and planning drives both the procurement of new ICT solutions through the production of statements of requirement ("SOR") and invitations to tender ("ITT") and is responsible for the initiation and management of ICT Programmes for strategic business change. Key outputs from design and planning are:
- ICT strategies, policies and plans
- the ICT overall architecture & management architecture
- feasibility studies, ITTs and SORs
- business cases
ICT deployment management
ICT deployment provides a framework for the successful management of design, build, test and roll-out (deploy) projects within an overall ICT programme. It includes many project management disciplines in common with PRINCE2, but has a broader focus to include the necessary integration of release management and both functional and non functional testing.
ICT operations management
ICT operations management provides the day-to-day technical supervision of the ICT infrastructure. Often confused with the role of incident management from service support, operations has a more technical bias and is concerned not solely with incidents reported by users, but with events generated by or recorded by the infrastructure. ICT operations may often work closely alongside incident management and the service desk, which are not-necessarily technical, to provide an 'operations bridge'. Operations, however should primarily work from documented processes and procedures and should be concerned with a number of specific sub-processes, such as: output management, job scheduling, backup and restore, network monitoring/management, system monitoring/management, database monitoring/management storage monitoring/management. Operations are responsible for the following:
- a stable, secure ICT infrastructure
- a current, up to date operational documentation library ("ODL")
- a log of all operational events
- maintenance of operational monitoring and management tools.
- operational scripts
- operational procedures
ICT technical support
ICT technical support is the specialist technical function for infrastructure within ICT. Primarily as a support to other processes, both in infrastructure management and service management, technical support provides a number of specialist functions: research and evaluation, market intelligence (particularly for design and planning and capacity management), proof of concept and pilot engineering, specialist technical expertise (particularly to operations and problem management), creation of documentation (perhaps for the operational documentation library or known error database). There are different levels of support under the ITIL structure, these being primary support level, secondary support level and tertiary support level, higher-level administrators being responsible for support at primary level.
The Known Error Database (KEDB) database contains all known error records. This database is created by problem management and used by incident management and problem management, and as part of service knowledge management systems.
Planning to implement service management
The ITIL discipline – planning to implement service management[17] attempts to provide practitioners with a framework for the alignment of business needs and IT provision requirements. The processes and approaches incorporated within the guidelines suggest the development of a continuous service improvement program (CSIP) as the basis for implementing other ITIL disciplines as projects within a controlled program of work. Planning to implement service management focuses mainly on the service management processes, but also applies generically to other ITIL disciplines. Components include:
- creating vision
- analysing organization
- setting goals
- implementing IT service management
Small-scale implementation
ITIL Small-scale implementation[18] provides an approach to ITIL framework implementation for smaller IT units or departments. It is primarily an auxiliary work that covers many of the same best practice guidelines as planning to implement service management, service support, and service delivery but provides additional guidance on the combination of roles and responsibilities, and avoiding conflict between ITIL priorities. The typical IT Organizational structure that maps to ITIL framework.

Related frameworks
A number of frameworks exist in the field of IT Service Management alongside ITIL.
Descendants
Microsoft Operations Framework
The Microsoft Operations Framework (MOF) is based on ITIL v2. While ITIL deliberately aims to be platform-independent, MOF is designed by Microsoft to provide a common management framework for its products. Microsoft has mapped MOF to ITIL as part of their documentation of the framework.[19]
FITS
The British Educational Communications and Technology Agency (BECTA) used ITIL as the basis for their development of Framework for ICT Technical Support (FITS). Their aim was to develop a framework appropriate for British schools, which often have very small IT departments. FITS became independent from BECTA in 2009 and is now maintained and supported by The FITS Foundation. FITS is now used in excess of a thousand schools in the UK, Australia and Norway as the standard for ICT Service Management in the Education sector (Video: What people are saying)
Other frameworks
The process framework of the ISO/IEC 20000 standard (previously BS 15000) is largely equivalent that of the Service Support and Service Delivery parts of ITIL Version 2.[20] While it is not possible for an organization to be certified as being ITIL compliant, certification of an organization is available for ISO/IEC 20000.[21]
COBIT is an IT governance framework and supporting toolset developed by ISACA. ISACA view ITIL as being complementary to COBIT. They see COBIT as providing a governance and assurance role while ITIL providing guidance for service management.[22]
The Business Process Framework (eTOM) published by the TeleManagement Forum offers a framework aimed at telecommunications service providers. In a joined effort, TM Forum and itSMF developed an Application Note to eTOM (GB921) that shows how the two frameworks can be mapped to each other. It addresses how eTom process elements and flows can be used to support the processes identified in ITIL.[23][24]
IBM Tivoli Unified Process (ITUP) is aligned with ITIL, but is presented as a complete, integrated process model compatible with IBM's products.
FitSM [25] is a standard for lightweight service management. Its process framework is quite similar to that of ISO/IEC 20000 and the Service Support and Service Delivery parts of ITIL version 2, but adopts Service Portfolio Management from later ITIL versions. FitSM contains several parts, including samples and templates for core ITSM documents, that are published under Creative Common licenses.
Certification
Individuals

The certification scheme differs between ITIL v2 and ITIL 2007/2011, and bridge examinations (now retired) allowed owners of v2 certificates to transfer to the new program. ITIL v2 offers three certification levels: Foundation, Practitioner and Manager. These were progressively discontinued in favor of the new scheme introduced along with the publication of the 2007 Edition. ITIL certification levels are now: Foundation, Intermediate, Expert and Master. In addition, the single-process practitioner certifications that were offered by OGC for version 2 have now been replaced and the offering expanded by what are known as complementary certifications.[26]
The ITIL certification scheme now offers a modular approach. Each qualification is assigned a credit value; so that upon successful completion of the module, the candidate is rewarded with both a certification and a number of credits. At the lowest level – Foundation – candidates are awarded a certification and two credits. At the Intermediate level, a total of additional 15 credits have to be earned. These credits may be accumulated in either a "Lifecycle" stream[note 1] or a "Capability" stream;[note 2] or combination thereof. Each Lifecycle module and exam is three credits. Each Capability module and corresponding exam is four credits. A candidate wanting to achieve the Expert level will have, among other requirements, to gain the required number of credits (22). That is accomplished with two from Foundations, then at least 15 from Intermediate, and finally five credits from the "Managing Across the Lifecycle" exam. Together, the total of 22 earned credits allows a person to request designation as an ITIL Expert. Advancing from the expert to the master level does not require additional credits, but does require at least five years of IT domain work experience and an extensive usage of ITIL practices.[27]
The complementary certifications also have point values, ranging from 0.5 to 1.5 credits, which can be applied towards ITIL Expert certification. However, only a maximum of six credits from complementary certifications can be applied towards the Expert certification.[28]
The ITIL Certification Management Board (ICMB) manages ITIL certification. The Board includes representatives from interested parties within the community around the world. Members of the Board include (though are not limited to) representatives from the UK Office of Government Commerce (OGC), APM Group (APMG), The Stationery Office (TSO), ITIL Examination Panel, Examination Institutes (EIs) and the IT Service Management Forum International (itSMF) as the recognised user group.[29]
Since the early 1990s, EXIN and ISEB had been setting up the ITIL based certification program, developing and providing ITIL exams at three different levels: Foundation, Practitioner and Manager. EXIN[30] and BCS/ISEB[31] (the British Computer Society) had from that time onwards been the only two examination providers in the world to develop formally acknowledged ITIL certifications, provide ITIL exams and accredit ITIL training providers worldwide. These rights were obtained from OGC, the British government institution and owner of the ITIL trademark. OGC signed over the management of the ITIL trademark and the accreditation of examination providers to APM Group in 2006. Now, after signing a contract with EXIN,[30] BCS/ISEB, Loyalist Certification Services ,PeopleCert Group and other certification bodies, APM Group has accredited them as official examination bodies, to offer ITIL exams and accredit ITIL training providers.
On July 20, 2006, the OGC signed a contract with the APM Group to become its commercial partner for ITIL accreditation from January 1, 2007.[32] APMG manage the ITIL Version 3 exams. APMG maintains a voluntary register of ITIL certified practitioners at their Successful Candidate Register.[33]
Since 2014, Axelos is the owner of the ITIL personnel certification scheme.[34] [35][36]
ITIL exams are administered by Accredited Training Organizations (ATOs), which are accredited by Examination Institute (EI).[37] The Examination Institutes, which issue the ITIL certificates, in turn need to be accredited by Axelos.[38]
Pins
Following the passing an APMG/EXIN exam in IT service management (based on ITIL), some people will wear a metal pin on their shirt or jacket. This badge, provided by the ITSMF with basic gold color is set in the form of the ITIL-logo. The ITIL pins consist of a small, diamond-like structure. The meaning and the shape of the diamond is meant to depict coherence in the IT industry (infrastructure as well). The four corners of the pin symbolise service support, service delivery, infrastructure management and IT management.
There are five colors of ITIL pins - each corresponds to the color of the associated core publication:
- ITIL Foundation Badge (Pastel Green). This ITIL lapel pin takes its color from the ITIL Service Strategy book and is awarded on successful completion of the ITIL Foundation exam.
- ITIL Intermediate Capability Badge (Burgundy). There are four ITIL Capability courses. (RCV, OSA, SOA, PPO). You are able to apply for this lapel pin once you have passed each exam. Some examination institutes such as APMG International will send the pins automatically with the candidate's certificate. This badge shares its color with the ITIL Service Transition book.
- ITIL Intermediate Lifecycle Badge (Teal). For each of the five ITIL Lifecycle courses (SS, SD, ST, SO, CSI), candidates receive this lapel pin after passing the exam. The color for this pin is based on the ITIL Service Operation book.
- ITIL Expert Badge (Lilac). This is currently the highest qualification available with ITIL. The lapel pin is awarded to a candidate who attains 22 credits through a combination of ITIL training courses. The pin takes its color from the ITIL Continual Service Improvement book.
- ITIL Master Badge (Purple, with the letter M in the middle). Currently in pilot phase this qualification has no training course or exam associated with it. To gain qualification as an ITIL Master, candidates have to have his/her work peer-reviewed by a panel of experts. Once an ITIL Expert has achieved this status, the ITIL Master can wear a lapel pin based on the color of the ITIL Service Design book, which also has a Gold M in the centre.
There are three colors of ITIL V2 pins:
- ITILv2 Foundation Badge (green)
- ITILv2 Practitioner Badge (blue)
- ITILv2 Manager Badge (red)
Exam candidates who have successfully passed the examinations for ITIL will receive their appropriate pin from APMG, EXIN or their certification provider regional office or agent.
Organizations
Organizations and management systems cannot claim certification as "ITIL-compliant". An organization that has implemented ITIL guidance in IT Service Management (ITSM), may be able to achieve compliance with and seek certification under ISO/IEC 20000. However, while relatively closely aligned, ISO/IEC 20000 and ITIL version 2 do not define identical processes.[39] This gap has become much wider with ITIL versions 2007 and 2011. ITIL now defines twice as many ITSM processes as ISO/IEC 20000 (26 compared to 13),[40] but there are also more subtle differences, e.g.[41]
- ISO/IEC 20000 only recognises the management of financial assets, not assets which include "management, organization, process, knowledge, people, information, applications, infrastructure and financial capital", nor the concept of a "service asset". So ISO/IEC 20000 certification does not address the management of "assets" in an ITIL sense.
- ISO20000 does not recognise Configuration Management System (CMS) or Service Knowledge Management System (SKMS), and so does not certify anything beyond Configuration Management Database (CMDB).
- An organization can obtain ISO/IEC 20000 certification without recognising or implementing the ITIL concept of Known Error, which is usually considered essential to ITIL.
Tools
Starting in 2009,[42] the APM Group, UK, established an ITIL Software Scheme (ISS) which allows IT Service Management software ITSM tool vendors to obtain endorsement through the Cabinet Office for an ITIL-based tool. This endorsement allows vendors to hold a valid ISS trademark licence and use the process compliant ITIL ‘swirl’ logo at a bronze, silver or gold level.
The ISS assessment operates through Licensed Software Assessors. Currently there are two companies listed as Licensed Software Assesors:[43] Pink Elephant, and Glenfis AG. In 1998[44] Pink Elephant released its PinkVerify assessment service, the 2011[45] version assesses a software tool against ITIL terminology, definitions, functionality and workflow requirements for the following 15 ITSM processes: Availability Management, Capacity Management, Change Management, Event Management, Financial Management, Incident Management, IT Service, Continuity Management, Knowledge Management, Problem Management, Release & Deployment Management, Request Fulfillment, Service Asset & Configuration Management, Service Catalog Management, Service Level Management, Service Portfolio Management. Currently there are three tools holding the PinkVerify 2011 certification for those 15 ITIL procesess:[46] CA Service Desk Manager Suite, Dexon Software V6 and SAP Solution Manager.
Criticism
ITIL has been criticised on several fronts, including:
- the books are not affordable for non-commercial users
- implementation and accreditation requires specific training
- debate over ITIL falling under BSM or ITSM frameworks
- the ITIL details are not aligned with the other frameworks like ITSM
Rob England (also known as "IT Skeptic") has criticised the protected and proprietary nature of ITIL.[47] He urges the publisher, Cabinet Office, to release ITIL under the Open Government Licence (OGL).[48]
CIO Magazine columnist Dean Meyer has also presented some cautionary views of ITIL,[49] including five pitfalls such as "becoming a slave to outdated definitions" and "Letting ITIL become religion." As he notes, "...it doesn't describe the complete range of processes needed to be world class. It's focused on ... managing ongoing services."
In a 2004 survey designed by Noel Bruton (author of "How to Manage the IT Helpdesk" and "Managing the IT Services Process"), organizations adopting ITIL were asked to relate their actual experiences in having implemented ITIL. Seventy-seven percent of survey respondents either agreed or strongly agreed that "ITIL does not have all the answers". ITIL exponents accept this, citing ITIL's stated intention to be non-prescriptive, expecting organizations to engage ITIL processes with existing process models. Bruton notes that the claim to non-prescriptiveness must be, at best, one of scale rather than absolute intention, for the very description of a certain set of processes is in itself a form of prescription.[50]
While ITIL addresses in depth the various aspects of service management, it does not address enterprise architecture in such depth. Many of the shortcomings in the implementation of ITIL do not necessarily come about because of flaws in the design or implementation of the service management aspects of the business, but rather the wider architectural framework in which the business is situated. Because of its primary focus on service management, ITIL has limited utility in managing poorly designed enterprise architectures, or how to feed back into the design of the enterprise architecture.
Closely related to the architectural criticism, ITIL does not directly address the business applications which run on the IT infrastructure; nor does it facilitate a more collaborative working relationship between development and operations teams. The trend toward a closer working relationship between development and operations is termed: DevOps. This trend is related to increased application release rates and the adoption of agile software development methodologies. Traditional service management processes have struggled to support increased application release rates – due to lack of automation – and/or highly complex enterprise architecture.
Some researchers group ITIL with lean, Six Sigma and Agile software development operations management. Applying Six Sigma techniques to ITIL brings the engineering approach to ITIL's framework. Applying Lean techniques promotes continuous improvement of the ITIL's best practices. However, ITIL itself is not a transformation method, nor does it offer one. Readers are required to find and associate such a method. Some vendors have also included the term Lean when discussing ITIL implementations, for example "Lean-ITIL". The initial consequences of an ITIL initiative tend to add cost with benefits promised as a future deliverable. ITIL does not provide usable methods "out of the box" to identify and target waste, or document the customer value stream as required by Lean, and measure customer satisfaction.
See also
- Application Services Library – A similar framework for Application Management
- Business Information Services Library (BiSL) – A similar framework for Information Management and Functional Management
- Granular configuration automation
- ISO/IEC 20000 – An international standard for IT service management
- Tudor IT Process Assessment – An framework for assessement of IT service management maturity
- Performance engineering
- RPR problem diagnosis
Notes
- ↑ The Lifecycle stream follows the ITIL core volumes; there are therefore 5 modules also called Service Strategy, Service Design, Service Transition, Service Operation and Continual Service Improvement.
- ↑ The Capability stream is more focused on process activities; the 4 modules available in 2013 are Operational support and analysis (OSA), Service offerings and agreements (SOA), Planning protection and optimization (PPO) and Release, control and validation (RCV).
References
- ↑ David Clifford; Jan van Bon (2008). Implementing ISO/IEC 20000 Certification: The Roadmap. ITSM Library. Van Haren Publishing. ISBN 90-8753-082-X.
- ↑ Office of Government Commerce (UK). CCTA and OGC. Retrieved on 2005-05-05 from http://www.ogc.gov.uk/index.asp?id=1878.
- ↑ Office of Government Commerce (UK). Retrieved on 2009-08-19 from http://www.ogc.gov.uk/guidance_itil.asp.
- ↑ "OGC withdrawal of ITIL version2". Archived from the original on 2010-01-23.
- 1 2 FSM. David Cannon (2011). ITIL Service Strategy 2011 Edition. The Stationery Office. ISBN 978-0113313044.
- 1 2 Lou Hunnebeck (2011). ITIL Service Design. The Stationery Office. ISBN 978-0113313051.
- 1 2 Stuart Rance (2011). ITIL Service Transition. The Stationery Office. ISBN 978-0113313068.
- 1 2 Randy A. Steinberg (2011). ITIL Service Operation. The Stationery Office. ISBN 978-0113313075.
- 1 2 Vernon Lloyd (2011). ITIL Continual Service Improvement. The Stationery Office. ISBN 978-0113313082.
- ↑ Cazemier, Jacques A.; Overbeek, Paul L.; Peters, Louk M. (2000). Security Management. The Stationery Office. ISBN 0-11-330014-X.
- ↑ Office of Government Commerce (2002). Application Management. The Stationery Office. ISBN 0-11-330866-3.
- ↑ "The DNA of APM - Event to Incident Flow". APM Digest. 4 June 2012.
- ↑ "Priorizing Gartner's APM Model: The APM Conceptual Framework". APM Digest. 15 March 2012.
- ↑ Office of Government Commerce (2000). Service Support. The Stationery Office. ISBN 0-11-330015-8.
- ↑ Office of Government Commerce (2001). Service Delivery. IT Infrastructure Library. The Stationery Office. ISBN 0-11-330017-4.
- ↑ Office of Government Commerce (2002). ICT Infrastructure Management. The Stationery Office. ISBN 0-11-330865-5.
- ↑ Office of Government Commerce (2002). Planning to Implement Service Management. The Stationery Office. ISBN 0-11-330877-9.
- ↑ Office of Government Commerce (2005). ITIL Small Scale Implementation. The Stationery Office. ISBN 0-11-330980-5.
- ↑ "Microsoft Operations Framework; Cross Reference ITIL and MOF 4.0". Microsoft Corporation. May 2009.
- ↑ Van Bon, Jan; Verheijen, Tieneke (2006), Frameworks for IT Management, Van Haren Publishing, ISBN 978-90-77212-90-5
- ↑ "ITIL ISO 20000". Itsmsolutions.com. 2006-03-21. Retrieved 2013-11-12.
- ↑ ISACA (2008), COBIT Mapping: Mapping of ITIL V3 With COBIT 4.1, ITGI, ISBN 978-1-60420-035-5
- ↑ Brooks, Peter (2006), Metrics for IT Service Management, Van Haren Publishing, pp. 76–77, ISBN 978-90-77212-69-1
- ↑ Morreale, Patricia A.; Terplan, Kornel (2009), "3.6.10.2 Matching ITIL to eTOM", CRC Handbook of Modern Telecommunications, Second Edition (2 ed.), CRC Press, ISBN 978-1-4200-7800-8
- ↑ "FitSM". FedSM Project. Retrieved 2012-12-12.
- ↑ "ITIL Complementary Qualifications". ITIL Official Site. Retrieved 2013-01-25.
- ↑ "ITIL Qualification Scheme Brochure". ITIL Official Website. Retrieved 2014-01-09.
- ↑ "ITIL Credit Profiler Tool". ITIL Official Site. Retrieved 2013-01-25.
- ↑ APMG (2008). "ITIL Service Management Practices: V3 Qualifications Scheme". Retrieved 24 February 2009.
- 1 2 "EXIN Exams". EXIN Exams. Retrieved 2010-01-14.
- ↑ "ISEB Professionals Qualifications, Training, Careers BCS – The Chartered Institute for IT". BCS. Retrieved 2010-01-14.
- ↑ Office of Government Commerce (2006). "Best Practice portfolio: new contracts awarded for publishing and accreditation services". Retrieved 19 September 2006.
- ↑ http://www.apmg-international.com/ITILSCRquery.asp
- ↑ "Axelos, Capita and the PRINCE2 Joint Venture". Advantage Learning. Retrieved 11 May 2014.
- ↑ "AXELOS to maximise profits in PRINCE2 and other best practice products", July 31, 2013
- ↑ "Axelos: The biggest shake-up of project management good practice in 13 years…".
- ↑ "Training Organization and Trainer Accreditation". Axelos. Retrieved 2012-12-12.
- ↑ "Examination Institutes". Axelos. Retrieved 2012-12-12.
- ↑ Jenny Dugmore; Alison Holt (2005). "ISO/IEC 20000 and ITIL – The Difference Explained".
- ↑ Pink Elephant (2011). "Definitive ITIL 2011 & 2007 Edition Process & Function Lists" (PDF). Retrieved 2014-12-23.
- ↑ Office of Government Commerce (2008). "Best Management Practice: ITIL V3 and ISO/IEC 20000" (PDF). Retrieved 24 February 2009.
- ↑ "ITIL Software Scheme - Operational Pilot Launch". The Official ITIL® Website. May 2009.
- ↑ "Licensed Software Assesors". The Official ITIL® Website. April 2014.
- ↑ "PinkVERIFY™ ITSM tool suite assessment service". Pink Elephant. April 2014.
- ↑ "PinkVERIFY 2011 Toolsets". Pink Elephant. April 2014.
- ↑ "PinkVERIFY 2011 Toolsets". Pink Elephant. May 2014.
- ↑ "Free ITIL®". The IT Skeptic. Retrieved 2013-11-12.
- ↑ "Open Government Licence". Nationalarchives.gov.uk. Retrieved 2013-11-12.
- ↑ Meyer, Dean, 2005. "Beneath the Buzz: ITIL", CIO Magazine, March 31, 2005
- ↑ Survey: "The ITIL Experience – Has It Been Worth It", author Bruton Consultancy 2004, published by Helpdesk Institute Europe, The Helpdesk and IT Support Show, and Hornbill Software.