Bridging (networking)
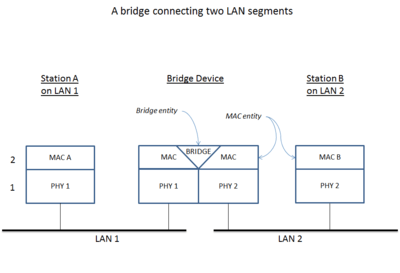
A network bridge is a computer networking device that creates a single aggregate network from multiple communication networks or network segments. This function is called network bridging.[1] Bridging is distinct from routing, which allows multiple different networks to communicate independently while remaining separate.[2] In the OSI model, bridging is performed in the first two layers, below the network layer (layer 3).[3] If one or more segments of the bridged network are wireless, the device is known as a wireless bridge and the function as wireless bridging.
There are four types of network bridging technologies: simple bridging, multiport bridging, learning or transparent bridging, and source route bridging.[4][5]
Simple bridging
A simple bridge connects two network segments, typically by operating transparently and deciding on a packet-by-packet basis whether or not to forward from one network to the other. A store and forward technique is typically used so, during forwarding, the packet integrity is verified on the source network and CSMA/CD delays are accommodated on the destination network. Contrary to repeaters that simply extend the maximum span of a segment, bridges only forward packets that are required to cross the bridge. Additionally, bridges reduce collisions by partitioning the collision domain.
Multiport bridging
A multiport bridge connects multiple networks and operates transparently to decide on a packet-by-packet basis whether and where to forward traffic. Like the simple bridge, a multiport bridge typically uses store and forward operation. The multiport bridge function serves as the basis for network switches.
Transparent bridging
A transparent bridge uses a forwarding database to send frames across network segments. The forwarding database starts empty - entries in the database are built as the bridge receives frames. If an address entry is not found in the forwarding database, the frame is flooded to all other ports of the bridge, flooding the frame to all segments except the one from which it was received. By means of these flooded frames, the destination network will respond and a forwarding database entry will be created.
In the context of a two-port bridge, one can think of the forwarding database as a filtering database. A bridge reads a frame's destination address and decides to either forward or filter. If the bridge determines that the destination node is on another segment on the network, it forwards (retransmits) the frame to that segment. If the destination address belongs to the same segment as the source address, the bridge filters (discards) the frame. As nodes transmit data through the bridge, the bridge establishes a filtering database of known MAC addresses and their locations on the network. The bridge uses its filtering database to determine whether a packet should be forwarded or filtered.
Transparent bridging can also operate over devices with more than two ports. As an example, consider a bridge connected to three hosts, A, B, and C. The bridge has three ports. A is connected to bridge port 1, B is connected to bridge port 2, C is connected to bridge port 3. A sends a frame addressed to B to the bridge. The bridge examines the source address of the frame and creates an address and port number entry for A in its forwarding table. The bridge examines the destination address of the frame and does not find it in its forwarding table so it floods it to all other ports: 2 and 3. The frame is received by hosts B and C. Host C examines the destination address and ignores the frame. Host B recognizes a destination address match and generates a response to A. On the return path, the bridge adds an address and port number entry for B to its forwarding table. The bridge already has A's address in its forwarding table so it forwards the response only to port 1. Host C or any other hosts on port 3 are not burdened with the response. Two-way communication is now possible between A and B without any further flooding in network.
Both source and destination addresses are used in this algorithm: source addresses are recorded in entries in the table, while destination addresses are looked up in the table and matched to the proper segment to send the frame to.
Digital Equipment Corporation (DEC) originally developed the technology in the 1980s.[6]
See also
References
- ↑ "Traffic regulators: Network interfaces, hubs, switches, bridges, routers, and firewalls" (PDF). Cisco Systems. 1999-09-14. Retrieved 2012-07-27.
- ↑ "What is a Network Switch vs. a Router?". Cisco Systems. Retrieved 2012-07-27.
- ↑ "RFC 1286 - Definitions of Managed Objects for Bridges". Tools.ietf.org. 1989-07-14. Retrieved 2013-10-19.
- ↑ "Local Area Networks: Internetworking". manipalitdubai.com. Archived from the original (PPT) on 2014-05-13. Retrieved 2012-12-02.
- ↑ "Bridging Protocols Overview" (PPT). iol.unh.edu. Retrieved 2012-12-02.
- ↑ "Transparent Bridging". Cisco Systems, Inc. Retrieved 2010-06-20.
Further reading
- "Internetworking Technology Handbook". cisco.com. Cisco Press. 1999-08-01. Retrieved 2015-12-20.